目的
一机多用
使用了Oracle甲骨文的orc-sanjose-1
参考
实现
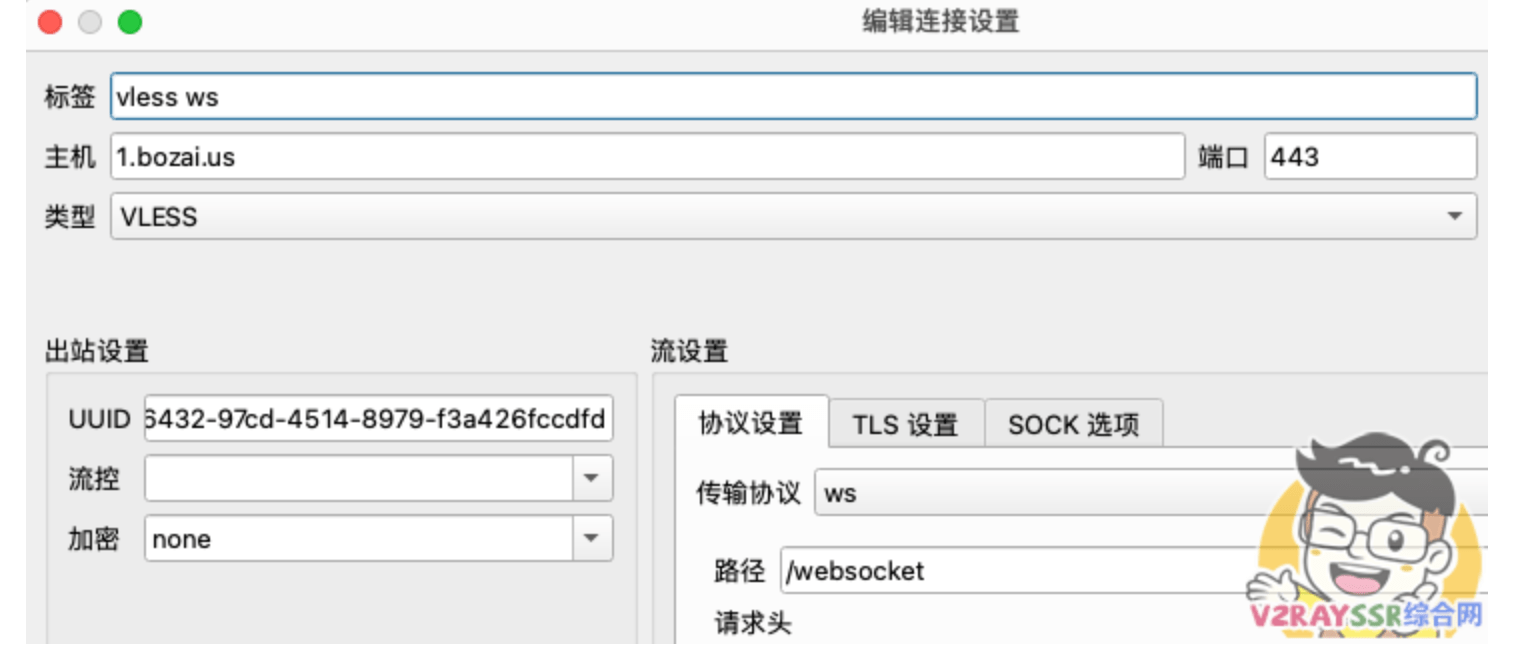
apt update -y && apt upgrade -y apt install curl tar nginx cron socat -y bash -c "$(curl -L https://github.com/XTLS/Xray-install/raw/main/install-release.sh)" @ install -u root # 粘贴到VPS运行即可生成 UUID, 如已有可略过 cat /proc/sys/kernel/random/uuid vi /usr/local/etc/xray/config.json # 把 c4616432-97cd-4514-8979-f3a426fccdfd 改成 你自己的uuid
{
"log": {
"loglevel": "warning"
},
"inbounds": [
{
"port": 443,
"protocol": "vless",
"settings": {
"clients": [
{
"id": "c4616432-97cd-4514-8979-f3a426fccdfd", // 填写你的 UUID
"flow": "xtls-rprx-direct",
"level": 0,
"email": "[email protected]"
}
],
"decryption": "none",
"fallbacks": [
{
"dest": 1310, // 默认回落到 Xray 的 Trojan 协议
"xver": 1
},
{
"path": "/websocket", // 必须换成自定义的 PATH
"dest": 1234,
"xver": 1
},
{
"path": "/vmesstcp", // 必须换成自定义的 PATH
"dest": 2345,
"xver": 1
},
{
"path": "/vmessws", // 必须换成自定义的 PATH
"dest": 3456,
"xver": 1
}
]
},
"streamSettings": {
"network": "tcp",
"security": "xtls",
"xtlsSettings": {
"alpn": [
"http/1.1"
],
"certificates": [
{
"certificateFile": "/usr/local/etc/xray/cert/cert.crt", // 换成你的证书,绝对路径
"keyFile": "/usr/local/etc/xray/cert/private.key" // 换成你的私钥,绝对路径
}
]
}
}
},
{
"port": 1310,
"listen": "127.0.0.1",
"protocol": "trojan",
"settings": {
"clients": [
{
"password": "Passw0rd", // 填写你的密码
"level": 0,
"email": "[email protected]"
}
],
"fallbacks": [
{
"dest": 80 // 或者回落到其它也防探测的代理
}
]
},
"streamSettings": {
"network": "tcp",
"security": "none",
"tcpSettings": {
"acceptProxyProtocol": true
}
}
},
{
"port": 1234,
"listen": "127.0.0.1",
"protocol": "vless",
"settings": {
"clients": [
{
"id": "c4616432-97cd-4514-8979-f3a426fccdfd", // 填写你的 UUID
"level": 0,
"email": "[email protected]"
}
],
"decryption": "none"
},
"streamSettings": {
"network": "ws",
"security": "none",
"wsSettings": {
"acceptProxyProtocol": true, // 提醒:若你用 Nginx/Caddy 等反代 WS,需要删掉这行
"path": "/websocket" // 必须换成自定义的 PATH,需要和分流的一致
}
}
},
{
"port": 2345,
"listen": "127.0.0.1",
"protocol": "vmess",
"settings": {
"clients": [
{
"id": "c4616432-97cd-4514-8979-f3a426fccdfd", // 填写你的 UUID
"level": 0,
"email": "[email protected]"
}
]
},
"streamSettings": {
"network": "tcp",
"security": "none",
"tcpSettings": {
"acceptProxyProtocol": true,
"header": {
"type": "http",
"request": {
"path": [
"/vmesstcp" // 必须换成自定义的 PATH,需要和分流的一致
]
}
}
}
}
},
{
"port": 3456,
"listen": "127.0.0.1",
"protocol": "vmess",
"settings": {
"clients": [
{
"id": "c4616432-97cd-4514-8979-f3a426fccdfd", // 填写你的 UUID
"level": 0,
"email": "[email protected]"
}
]
},
"streamSettings": {
"network": "ws",
"security": "none",
"wsSettings": {
"acceptProxyProtocol": true, // 提醒:若你用 Nginx/Caddy 等反代 WS,需要删掉这行
"path": "/vmessws" // 必须换成自定义的 PATH,需要和分流的一致
}
}
}
],
"outbounds": [
{
"protocol": "freedom"
}
]
}申请ssl证书
# 在cloudflare等上面设置好 域名 -> ip的映射 # 下载用于获取ssl证书的脚本 curl https://get.acme.sh | sh export CF_Email="[email protected]" export TLD_DOMAIN="yyy.xxx.com" export KEY_FILE_PATH="/usr/local/etc/xray/cert" export WEB_ROOT_PATH="/var/www/html" # 获取证书 ~/.acme.sh/acme.sh --register-account -m ${CF_Email} mkdir -p ${KEY_FILE_PATH} # 通过http访问验证方式; 不需要key和email ### 一定要确保webroot是当前nginx所对应的目录,不然就无法验证了 ~/.acme.sh/acme.sh --issue -d ${TLD_DOMAIN} --webroot ${WEB_ROOT_PATH} ~/.acme.sh/acme.sh --installcert -d ${TLD_DOMAIN} \ --key-file ${KEY_FILE_PATH}/private.key \ --fullchain-file ${KEY_FILE_PATH}/cert.crt ~/.acme.sh/acme.sh --upgrade --auto-upgrade chmod -R 755 ${KEY_FILE_PATH}
重启服务 – 有时候还要重启机器
systemctl restart xray # 重启xray服务 systemctl status xray # 查看xray运行状态 systemctl enable nginx # 开启自动 systemctl restart nginx # 重启nginx ### just in case # /var/log/nginx/access.log # /etc/nginx/nginx.conf # /etc/nginx/sites-enabled/default
下载伪装网站
# export WEB_ROOT_PATH="/var/www/html"
rm -rf ${WEB_ROOT_PATH}/*
cd /${WEB_ROOT_PATH}
wget https://github.com/V2RaySSR/Trojan/raw/master/web.zip
unzip web.zip
systemctl restart nginx梯子配置
vmess+ws
- name: "V2_美西甲骨文 orc-sanjose-1"
type: vmess
server: orc-sanjose-1.yyy.xxx
port: 443
uuid:
alterId: 0
cipher: auto
tls: true
network: ws #如果选了h2,就填h2
ws-headers:
Host: orc-sanjose-1.yyy.xxx
ws-path: /vmesswsvless + xtls + tcp (据说性能最强)
vless://[email protected]:443?security=xtls&encryption=none&headerType=none&type=tcp&flow=xtls-rprx-splice#orc-sanjose-1+vless+xtls

trojan
- name: "Trojan_美西甲骨文 orc-sanjose-1" type: trojan server: orc-sanjose-1.yyy.xxx port: 443 password: Passw0rd skip-cert-verify: true

vless+ws+tls